Request a demo or technical briefing
For procurement or partnership inquiries, include your organization name, point of contact, and a brief description of your needs.
Boeing delivers robust solutions for secure data transfer and cyber situational awareness through its HardwareWall® (HWW) and the Security Monitoring Infrastructure System (SMIS) offerings. HWW enables secure, policy-enforced data transfer across classification domains, featuring virus protection, content filtering, and bidirectional transfers between TS/SCI and Unclassified networks. SMIS enhances network security with advanced detection capabilities, including signature detection, automated anomaly detection, and behavior-based analytics. Both systems offer flexible deployment options, low operational costs, and comprehensive support, ensuring organizations can effectively manage security risks while maintaining operational efficiency across diverse environments.
HardwareWall® (HWW) is Boeing’s Raise the Bar (RTB) cross-domain solution (CDS) designed for secure and efficient data transfer across disconnected classification domains. With over 20 years of deployment experience, HWW integrates physical separation, virus protection, and content filtering to meet government standards. It supports various platforms, enabling bidirectional transfers between TS/SCI and Unclassified networks. With multiple form factors, HWW offers high throughput, low operational overhead, and minimal maintenance, ensuring mission effectiveness and cost efficiency. Its scalable design meets both enterprise and tactical needs, facilitating faster intelligence sharing for real-time operations.

Physical network separation and hardware isolation create distinct networks and dedicated devices for different classification levels, ensuring sensitive data remains isolated from less secure environments.
Enforced one-way physical transfer using FPGA diodes allows data to flow in only one direction, preventing any backflow and maintaining network integrity.
Ensures accurate classification and assessment of information, while RAIN filters provide an impassable layer of protection for authorized data transmission.
Multiple barriers and mandatory control policies prevent unauthorized access and ensure that only authorized users can access sensitive information.
A single-source hardware and software supply chain enhances security by simplifying provisioning and ensuring consistent security measures across all components.
Independently tested to meet rigorous standards such as MIL-STD-810G, MIL-STD-461G, DO-160G and TEMPEST. This ensures that it can withstand harsh environmental conditions and electromagnetic interference, making it suitable for military and aerospace applications.
With a compact and lightweight chassis, the systems are designed to fit in 1U or 2U racks. It offers multiple mounting options, making it versatile for installation in aircraft, vehicles and maritime platforms.
The system features miniaturized removable SSDs that facilitate rapid servicing and enable fast, secure data movement. This design is particularly advantageous in constrained Size, Weight and Power (SWaP) environments, ensuring efficient operation without compromising performance.
Designed for fast setup, the system reduces integration time and allows for quicker deployment and rapid readiness in operational environments.
With a similar installation and configuration process for all supported hardware units, the system simplifies management tasks and enhances overall operational efficiency.
The commercial off-the-shelf design allows for the creation of cost-effective cloned systems, making it easier to scale operations as needed.
Customization aligns with mission policy and operational workflows, while also being built and customized to meet program-specific needs. This adaptability ensures that the system effectively supports diverse mission objectives and enhances operational effectiveness.
Installation, integration and accreditation (A&A) support are provided to facilitate a smooth deployment process, system setup and compliance with regulatory standards.
Comprehensive user training and documentation are available, covering architecture, operations and maintenance.
Flexible maintenance and field support options are offered via phone, email or onsite assistance, allowing users to choose the most convenient method that minimizes downtime and maintains operational readiness.
Information assurance consulting services are available for design, selection and network analysis, ensuring that security considerations are integrated into every aspect of the system.
With long-standing accreditation experience dating back to the first TS→U system in 2003, the team has a deep understanding of compliance requirements.
Providing users with a reliable and secure operating environment to ensure organizations can leverage the latest features and security updates.
Achieving RTB approval provides an extensive body of evidence that accelerates the accreditation and authorization (A&A) process for customers.
HWW supports unclassified/High Threat Networks, secret, and top-secret/TS/SCI configurations, certified up to PL-5 for bidirectional transfers.
Typical deployments average around 180 days from award to operational fielding, depending on customization and A&A timelines.
Yes — HWW supports both file-based and streaming data across multiple validated formats; the fixed-format filter can support additional fixed-format data formats.
HWW is tested to MIL-STD-810G, MIL-STD-461G, DO-160G and TEMPEST standards.
Yes. Boeing provides configuration, integration, training, documentation, A&A support and flexible maintenance options.
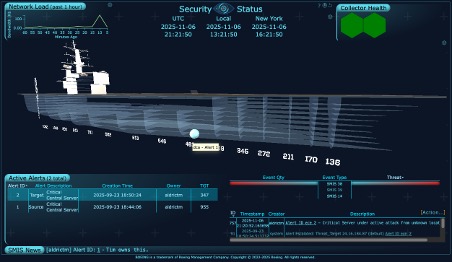
SMIS is a high-fidelity network and cyber situational awareness tool developed by Boeing, supported by 11 patents on core technologies. It operates on commodity hardware, scaling from single enclave deployments to global installations, and can function stand-alone or integrate into existing tool chains. SMIS features multisense detection with four independent families, patent-protected algorithms for advanced threat visibility, and flexible deployment options. With low operational costs, faster threat detection, reduced operator fatigue, and forensics-ready capabilities, SMIS allows organizations to start small and scale efficiently while maximizing security effectiveness.
Utilizes Snort-based deep packet signature scanning to identify well-known threats and is complemented by other detection methods to ensure comprehensive coverage.
Includes over 13 plug-and-play detectors that analyze unencrypted packet headers for various issues like rogue IPs and bandwidth spikes. This feature requires no user configuration, allowing for immediate issue detection.
Offers a flexible rule syntax for monitoring traffic based on IPs, ports and VLANs. This allows users to define acceptable communications and detect deviations effectively.
Continuously establishes baselines and employs patented APT pattern detection to identify stealthy threats. This includes bandwidth prediction and failed beacon analysis for enhanced threat visibility.
An algorithmic correlation engine consolidates events into prioritized alerts, reducing operator workload by filtering false positives and ranking threats effectively.
Built with HTML5/CSS/JavaScript, the interface supports all mainstream browsers, providing a user-friendly experience to enhance accessibility and usability.
Features five built-in roles and unlimited custom roles to ensure proper separation of duties and control user access based on their roles.
Offers a training mode for operators to familiarize themselves with the system on live data to help reduce the learning curve and improve operational readiness.
Allows users to navigate from alerts to raw packet views with a single click. This streamlined process enhances efficiency and reduces response times.
Provides over 80 unique displays, including dashboards and status maps, to visualize data effectively. This variety aids in quick decision-making and situational awareness.
Acts as the central server and human interface, storing events and performing real-time analysis. Each deployment includes at least one SUS, with options for redundancy.
Monitors multiple passive taps and performs signature scanning and raw packet storage. This headless sensor enhances data collection capabilities without user intervention.
Supports both small and large installations, from a single SUS and FDC to extensive global deployments to enable organizations to scale according to their needs.
Runs on standard 64-bit CPUs with recommended specifications, allowing organizations to utilize existing infrastructure.
Requires a minimum of 8GB RAM and 250GB storage, with recommendations for higher specifications for optimal performance.
FDCs can be compact devices or larger setups, accommodating different monitoring needs.
Accepts passive taps from various hardware vendors, ensuring flexibility in packet acquisition and allowing for easy integration into existing systems.
Assumes that packet feed provisioning is managed by the customer, which is standard for monitoring solutions and allows organizations to maintain control over their network feeds.
Eliminates per-seat or per-device scaling fees, with licensing based solely on the number of SUSs and FDCs deployed and promoting scalability without financial penalties.
Provides continuous updates and support through an annual maintenance fee, ensuring the system remains current, effective and reliable.
No additional commercial database or third-party licensing is required, significantly reducing total cost of ownership. Automation features further decrease system administration overhead, making SMIS a cost-effective solution.


For procurement or partnership inquiries, include your organization name, point of contact, and a brief description of your needs.